TL;DR
Researchers Ilja and Michael Smith audited FreeBSD's jail attack surface and identified roughly 50 vulnerabilities across multiple kernel subsystems. They built proof-of-concept exploits, demonstrated real escapes in a talk at 39c3, and say they are working with the FreeBSD security team on fixes.
What happened
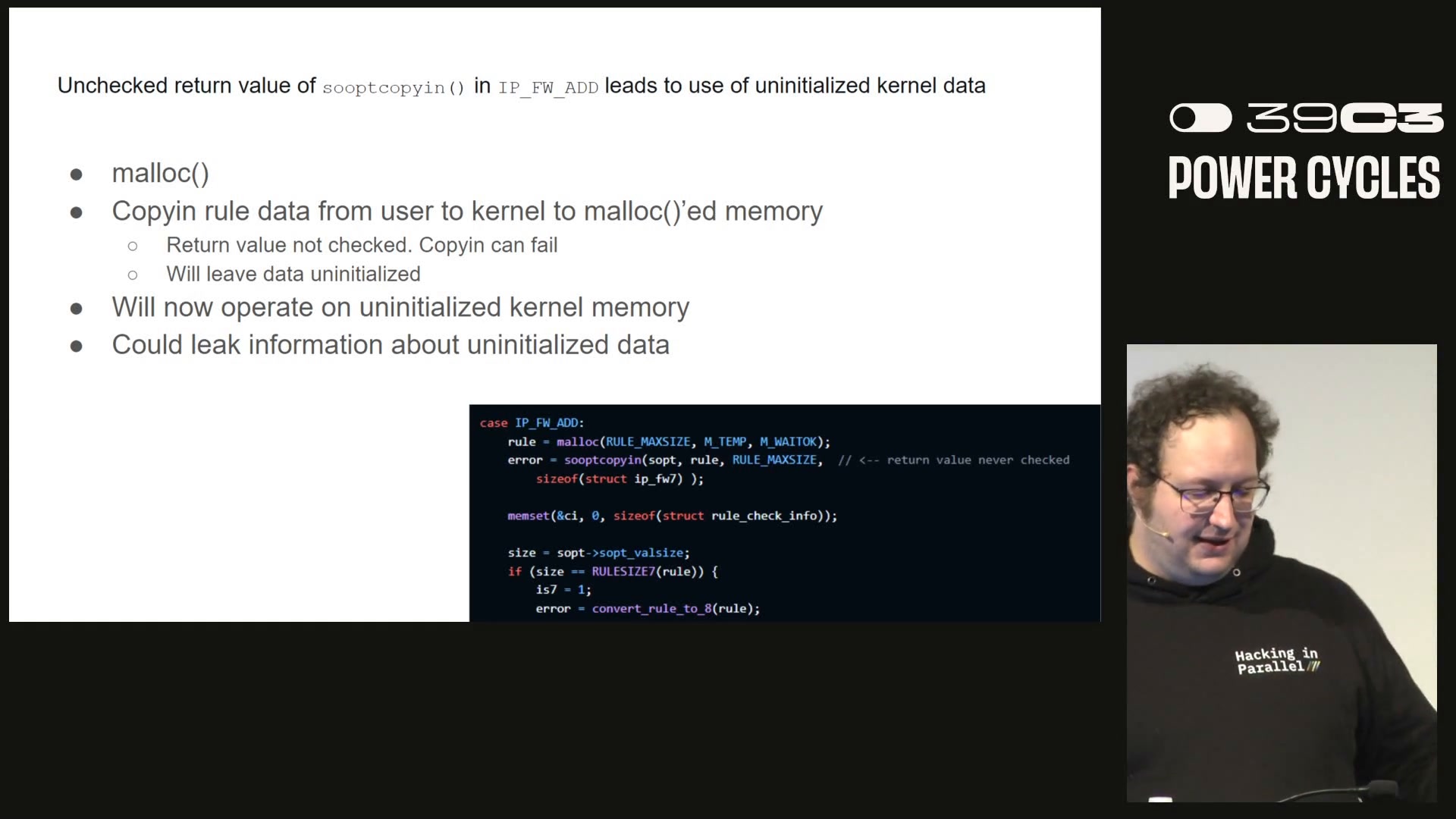
At the 39c3 conference, presenters Ilja and Michael Smith released a security study examining the strength of FreeBSD’s jail isolation. The researchers performed a large-scale audit of kernel code paths reachable from inside a jailed process, focusing on privileged operations, capabilities and interfaces that remain accessible from within a jail. Their review turned up about 50 distinct issues across several kernel subsystems, including buffer overflows, information leaks, unbounded allocations and reference-counting errors. The team developed proof-of-concept exploits and tools to demonstrate some of these weaknesses and showed demos of actual jail escapes during the talk. They say they have disclosed their findings to the FreeBSD security team and are collaborating on fixes. The talk covers their methodology, tooling, selected exploit demonstrations, and broader lessons for operating-system-level container isolation.
Why it matters
- FreeBSD jails are widely used for hosting, container frameworks and security sandboxes, so flaws could affect deployed isolation environments.
- Vulnerabilities found include memory-safety and logic errors that can lead to crashes or privilege escalation beyond the jail.
- The research highlights how complexity in a mature kernel feature increases the attack surface for containment mechanisms.
- Demonstrated proof-of-concept exploits show that theoretical issues can be turned into practical escape techniques, driving the need for coordinated fixes.
Key facts
- Presentation delivered at the 39c3 conference.
- Speakers: Ilja and Michael Smith.
- Runtime: the recorded talk is 59 minutes and 16 seconds long.
- Researchers audited kernel code paths reachable from inside FreeBSD jails.
- Approximately 50 distinct issues were identified across multiple kernel subsystems.
- Reported flaw types include buffer overflows, information leaks, unbounded allocations and reference-counting errors.
- Proof-of-concept exploits and tools were developed and some escape demos were shown in the talk.
- Findings were responsibly disclosed to the FreeBSD security team and the researchers say they are collaborating on fixes.
- The talk and related materials are published under a Creative Commons BY 4.0 license and downloadable in multiple formats and languages.
What to watch next
- FreeBSD security advisories and patch releases for fixes related to the disclosed issues — not confirmed in the source
- Upstream kernel commits or changelogs that address the specific vulnerabilities — not confirmed in the source
- Follow-up writeups or code releases from the researchers that expand on the tooling and exploits — not confirmed in the source
Quick glossary
- FreeBSD jail: An operating-system-level mechanism on FreeBSD that isolates processes and filesystem views to provide container-like environments.
- Kernel: The core part of an operating system that manages hardware, memory, processes and privileged operations.
- Proof-of-concept (PoC) exploit: Code or techniques developed to demonstrate that a vulnerability can be exploited in practice.
- Privilege escalation: When an attacker gains higher-level permissions than initially available, potentially breaking containment or sandboxing.
- Buffer overflow: A class of memory-safety vulnerability where a program writes more data to a buffer than it can hold, often exploitable to alter control flow.
Reader FAQ
Who conducted this research?
The talk and research were presented by Ilja and Michael Smith.
How many issues did the researchers report?
They reported roughly 50 distinct issues across multiple kernel subsystems.
Did they build exploits to demonstrate the problems?
Yes. The team developed proof-of-concept exploits and tools and showed demos of jail escapes during the talk.
Has FreeBSD released patches for the issues?
Not confirmed in the source.
Are the findings relevant to other container or OS-level isolation systems?
The presenters drew lessons for other OS container systems and discussed broader challenges in maintaining isolation.
Escaping Containment: A Security Analysis of FreeBSD Jails ilja and Michael Smith Video Player 15 30 00:00 | 59:16 None eng (auto) 1.00x eng 1080p h264-hd (mp4) deu 1080p h264-hd…
Sources
- Escaping Containment: A Security Analysis of FreeBSD Jails
- Escaping Containment: A Security Analysis of FreeBSD Jails
- 262179 – Prevent jail escaping via shared nullfs
- Playlist for "39C3: Power Cycles" – media.ccc.de
Related posts
- Sword-wielding contractor runs private squatter-removal service in Oakland
- Holiday disruption: ‘MongoBleed’ zlib bug (CVE-2025-14847) in MongoDB now exploited
- Two cybersecurity workers plead guilty in 2023 ransomware extortion case