TL;DR
A pair of researchers presented a 59-minute analysis of FreeBSD jails that identified roughly 50 kernel-level issues accessible from inside a jail. They produced proof-of-concept exploits, disclosed the findings to the FreeBSD security team, and are working with maintainers on fixes.
What happened
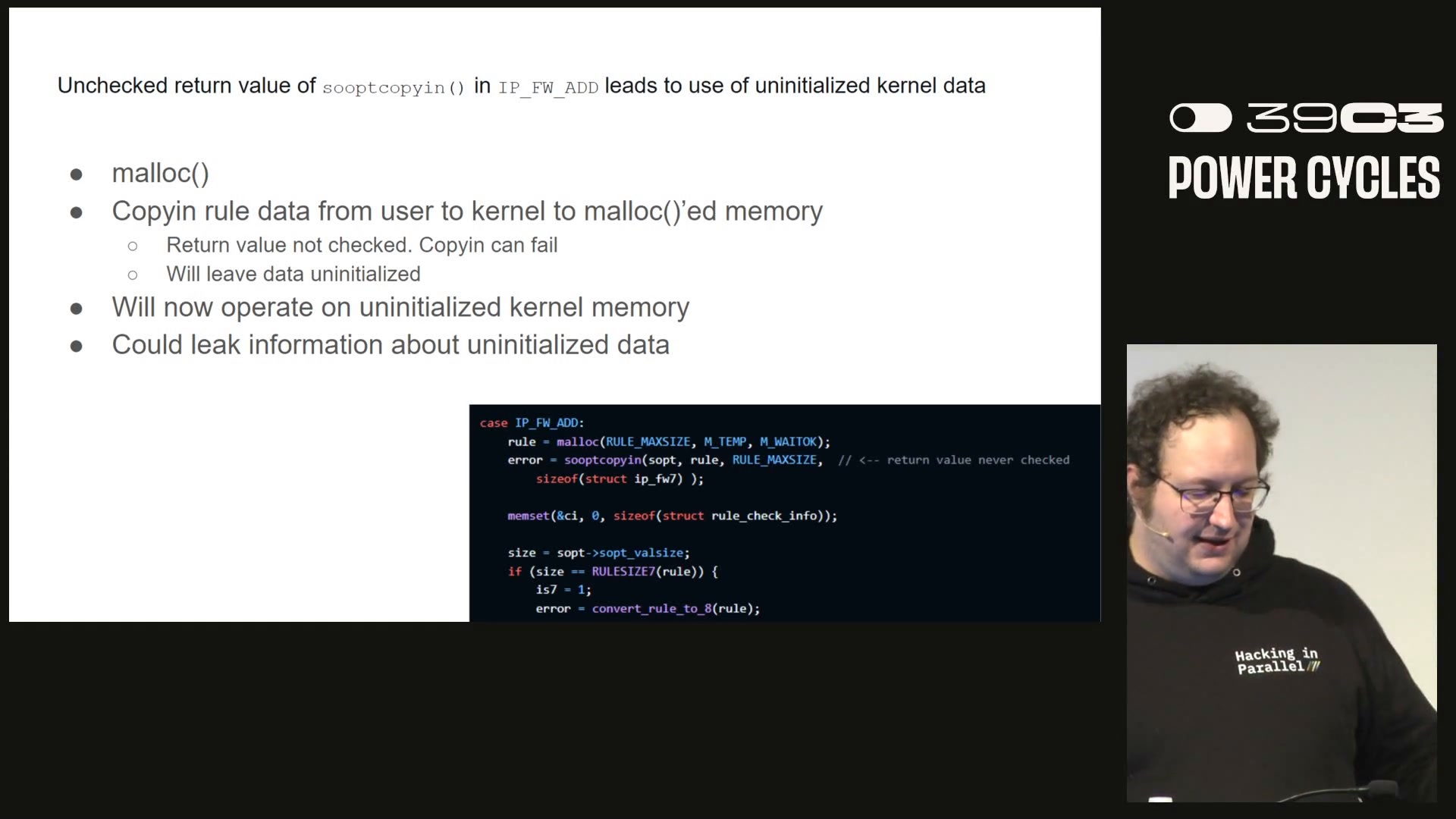
At the 39c3 event, researchers ilja and Michael Smith presented an in-depth security audit of FreeBSD's jail facility, the OS-level isolation mechanism used for hosting and sandboxing. They systematically reviewed kernel code paths reachable from a jailed process, focusing on privileged operations, capabilities and interfaces still exposed inside jails. The audit uncovered about 50 distinct issues across multiple kernel subsystems, including buffer overflows, information leaks, unbounded allocations and reference-counting errors; several of these could lead to crashes or privilege escalation beyond the jail boundary. The presenters developed proof-of-concept exploits and tooling to demonstrate some escapes in practice. The team says it has responsibly disclosed the findings to the FreeBSD security group and is collaborating on remediation. The talk covers their methodology, tooling, selected demos and broader lessons for maintaining kernel isolation.
Why it matters
- FreeBSD jails are widely used for hosting, containers and security sandboxes; kernel weaknesses accessible from within a jail threaten that isolation model.
- Multiple classes of bugs (memory safety, races, logic errors) were found, showing that diverse bug types can undermine OS-level containment.
- Proof-of-concept exploits illustrate practical attack paths, increasing the urgency for fixes rather than theoretical concern.
- The findings highlight long-term maintenance challenges for large, mature kernel features and signal attention for other OS container systems.
Key facts
- Presentation title: Escaping Containment: A Security Analysis of FreeBSD Jails.
- Speakers listed as ilja and Michael Smith; session length ~59 minutes.
- Researchers audited kernel code paths reachable from inside a FreeBSD jail.
- Approximately 50 distinct issues were identified across multiple kernel subsystems.
- Issue types reported include buffer overflows, information leaks, unbounded allocations and reference-counting errors.
- The team developed proof-of-concept exploits and demonstration tooling for some vulnerabilities.
- Findings were responsibly disclosed to the FreeBSD security team and collaboration on fixes is ongoing.
- The talk includes methodology, tooling details, demos of real escapes, and lessons for hardening isolation boundaries.
- Video and audio files with multiple language tracks are available for download; the release is licensed under CC BY 4.0.
What to watch next
- Release of security patches or advisories from the FreeBSD security team addressing the disclosed issues.
- Follow-up disclosures or technical write-ups from the researchers detailing specific vulnerabilities and mitigations.
- Not confirmed in the source: whether individual CVE identifiers have been or will be assigned to the discovered issues.
Quick glossary
- FreeBSD jail: An OS-level isolation mechanism in FreeBSD that restricts processes to a separate namespace and resource view to provide sandboxing and multi-tenancy.
- Kernel attack surface: The set of kernel interfaces, operations and code paths that can be invoked by user-space processes and thus are subject to exploitation risk.
- Proof-of-concept (PoC) exploit: A demonstration showing how a vulnerability can be abused to achieve an undesirable outcome, such as privilege escalation or code execution.
- Memory safety: Property of code that prevents common errors like buffer overflows, use-after-free and invalid memory accesses that can lead to exploitation.
- Reference counting: A memory-management technique where objects track the number of references to them; errors can produce leaks or premature frees leading to instability or exploitation.
Reader FAQ
Did the researchers publish exploit code or tools publicly?
Not confirmed in the source.
Have fixes been released for the reported issues?
The researchers said they have responsibly disclosed the findings and are collaborating with the FreeBSD security team; whether fixes are already released is not confirmed in the source.
Which FreeBSD kernel subsystems were affected?
The source states that issues spanned multiple kernel subsystems but does not list specific subsystems.
How can operators protect jailed workloads now?
Not confirmed in the source.
What is the license for the talk materials?
The talk is licensed under Creative Commons Attribution 4.0 (CC BY 4.0), according to the source.
Escaping Containment: A Security Analysis of FreeBSD Jails ilja and Michael Smith Video Player 15 30 00:00 | 59:16 None eng (auto) 1.00x eng 1080p h264-hd (mp4) deu 1080p h264-hd…
Sources
- Escaping containment: A security analysis of FreeBSD jails
- Major security audit of critical FreeBSD components now …
- Chapter 17. Jails and Containers
- Addressing Vulnerabilities Through Synacktiv's Code Audit
Related posts
- Former U.S. cybersecurity experts plead guilty in BlackCat ransomware case
- Honey’s Dieselgate: Detecting When Testers Are Identified and Tricked
- Escaping Containment — Security Analysis Reveals Jail Escape Paths in FreeBSD