TL;DR
Attackers are abusing compromised SendGrid customer accounts to send politically charged phishing emails that pass authentication checks. The messages use provocative opt-out buttons to harvest credentials and even 2FA codes in real time.
What happened
Over recent months, threat actors have been sending convincing phishing messages that appear to come from SendGrid customers. Rather than spoofing sendgrid.com, the attackers send mail through legitimate SendGrid customer accounts that have been compromised (by credential stuffing, password reuse and similar methods), so messages pass SPF and DKIM checks and bypass many spam defenses. The scams use culturally divisive lures—fake announcements about Pride footers, Black Lives Matter themes, a supposed “Support ICE” donation button, a sudden Spanish-language switch, or account termination notices—to provoke recipients into clicking an opt-out or preference link. Those links lead to counterfeit SendGrid login pages that validate credentials against SendGrid’s API in real time and capture passwords and two-factor codes. Security researchers earlier labeled this technique “Phishception,” and reporting on similar abuse stretches back several years. Recommended mitigations noted by the author include enabling 2FA, using unique passwords, auditing API keys/sender identities, and avoiding links in suspicious messages.
Why it matters
- Emails sent through compromised SendGrid accounts can pass standard authentication checks, making them look legitimate.
- Politically charged lures exploit emotional reactions, increasing the likelihood of credential theft.
- Captured credentials and 2FA codes let attackers commandeer more SendGrid accounts, enabling further abuse.
- Business email infrastructure abuse can propagate attacks across many organizations and targets.
Key facts
- Attackers are compromising real SendGrid customer accounts and sending phishing emails from those accounts.
- Because the mail is sent through SendGrid infrastructure, messages can pass SPF and DKIM validation.
- Phishing themes observed include fake Pride footers, Black Lives Matter commemorations, a bogus ‘Support ICE’ button, a Spanish language switch, and account-termination notices.
- Opt-out or preference links in these emails are the primary credential-theft mechanism.
- The counterfeit login pages can validate credentials against SendGrid’s API in real time and capture 2FA codes.
- Netcraft researchers called this pattern “Phishception” in 2024; Brian Krebs documented related abuse in 2020.
- Twilio, SendGrid’s parent company, has discussed requiring two-factor authentication but broad enforcement has been slow.
- Recommended protections for SendGrid customers: enable two-factor authentication, use unique passwords, and audit for unauthorized API keys or sender identities.
- A suggested Gmail filter can delete messages that mention SendGrid but do not originate from sendgrid.com or twilio.com.
What to watch next
- Whether Twilio/SendGrid will mandate two-factor authentication for all customers: not confirmed in the source
- Emergence of new politically themed phishing variations and how quickly attackers adapt: not confirmed in the source
- Any public disclosure from Twilio/SendGrid on measures taken to stop account compromise: not confirmed in the source
Quick glossary
- Phishing: Fraudulent messages designed to trick recipients into revealing credentials or other sensitive information.
- SPF: Sender Policy Framework — an email authentication method that helps mail receivers verify that messages originate from authorized mail servers.
- DKIM: DomainKeys Identified Mail — an email authentication technique that uses cryptographic signatures to confirm a message’s origin and integrity.
- Two-factor authentication (2FA): A security method that requires two separate forms of verification (typically a password plus a second factor) before granting account access.
- Credential stuffing: An attack in which breached username/password pairs are reused across multiple services to find valid logins.
Reader FAQ
Are these emails actually from SendGrid?
No. They are sent through compromised SendGrid customer accounts, not from sendgrid.com itself.
How do the phishers steal credentials and 2FA codes?
Links take victims to fake SendGrid login pages that validate credentials against the real API in real time and capture submitted passwords and codes.
What should SendGrid customers do right now?
Enable two-factor authentication, use unique passwords, and check for unauthorized API keys or sender identities.
Is this the work of a state actor?
The source says attribution is uncertain; it could be state-backed actors or independent operators with knowledge of American political fault lines.
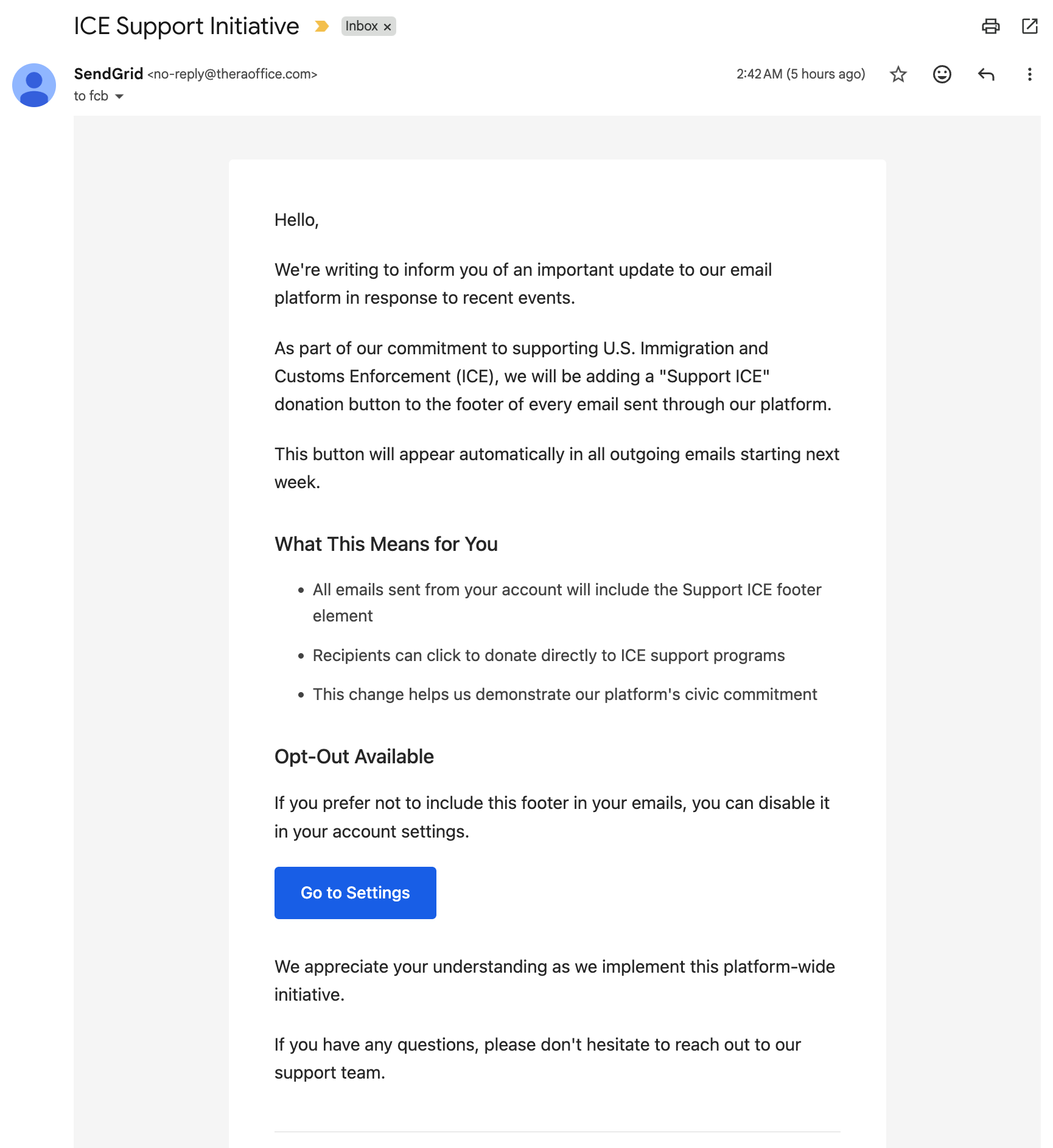
SendGrid isn’t emailing you about ICE or BLM. It’s a phishing attack. Written by Fred on January 9, 2026 For the past several months, I’ve been receiving and then ignoring…
Sources
- SendGrid isn’t emailing about ICE or BLM – it’s a phishing attack
- SendGrid is abused to host phishing attacks impersonating …
- Active Phishing Campaign: Twilio SendGrid Abuse – Agari
- Phishing attack uses compromised SendGrid accounts to …
Related posts
- Cloudflare CEO Matthew Prince Criticizes Italy’s $17M Fine, Threatens Pullback
- Vietnam enacts new rule: all online video ads must be skippable in 5 seconds
- U.S. Adds Seven Nations to $15,000 Visitor Visa Bond Requirement