TL;DR
KrebsOnSecurity celebrates its 16th anniversary, summarizing a year of investigations into entities that enabled large-scale cybercrime, phishing operations, and powerful botnets. Notable coverage in 2024–25 included reporting on bulletproof hosting, payment processors, DDoS attacks, and emerging botnet activity.
What happened
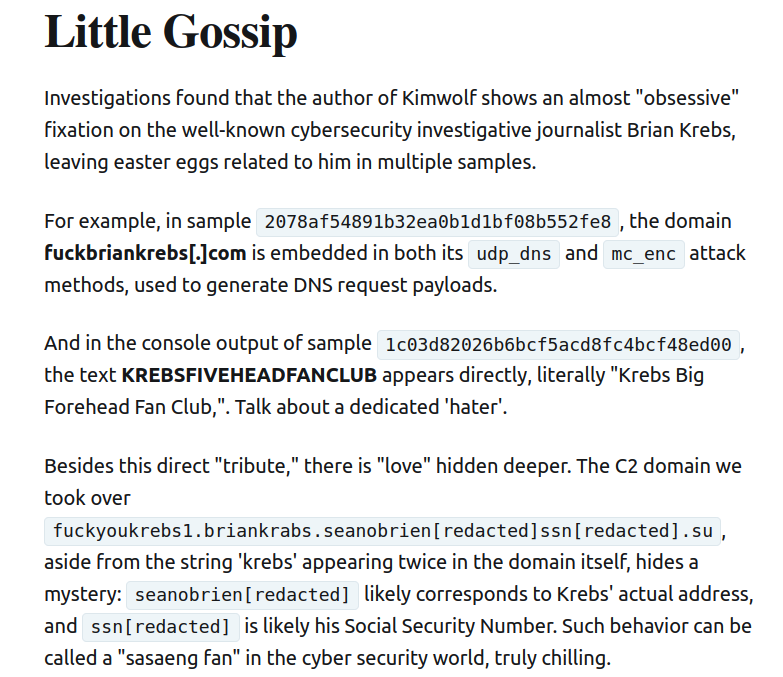
On December 29, 2025, KrebsOnSecurity marked its 16th year of publishing investigative work focused on cybercrime infrastructure and abuse. Over the past two years the site traced the activity and ownership of Stark Industries Solutions Ltd., a bulletproof hosting provider tied to Kremlin-linked operations and later sanctioned by the EU, while noting its proprietors have moved assets and rebranded. Reporting also followed Cryptomus, a Canada-registered payments firm that was fined $176 million by Canadian regulators in October 2025 for anti-money-laundering violations. Coverage connected cracked master passwords from a LastPass breach to a string of high-value cryptocurrency thefts, documented multiple voice-phishing and smishing operations, and profiled dodgy content-delivery and proxy services such as Funnull. The site was targeted by record DDoS attacks in June attributed to the Aisuru botnet, and recent analysis points to an even larger Android botnet called Kimwolf. KrebsOnSecurity says it will publish a 2026 series examining Kimwolf’s origins and related security risks.
Why it matters
- Investigations expose the intermediaries — hosting, payment, and proxy services — that enable global cybercrime ecosystems.
- Follow-up enforcement (sanctions, fines, arrests) shows some accountability but also highlights limits when operators rebrand or move assets.
- Large-scale botnets and evolving phishing tactics continue to escalate risk to online services, cryptocurrency holders, and consumers.
- Public reporting can drive law-enforcement action and help defenders prioritize mitigation and notifications for affected systems.
Key facts
- KrebsOnSecurity published its 16th-anniversary post on December 29, 2025.
- Stark Industries Solutions Ltd. was profiled as a bulletproof hosting provider that emerged shortly before Russia’s invasion of Ukraine and later faced EU sanctions; reporting says owners have rebranded and moved assets.
- Cryptomus, a Canadian-registered financial firm, was fined $176 million by Canadian financial regulators in October 2025 for anti-money-laundering violations.
- Researchers and U.S. federal agents have linked several six-figure cryptocurrency thefts to master passwords stolen from LastPass in 2022.
- KrebsOnSecurity documented extensive voice phishing crews abusing legitimate services at Apple and Google to perpetrate cryptocurrency thefts.
- The site endured what was described as the largest DDoS attack Google had ever mitigated at the time in June 2025; Aisuru, an IoT botnet, was blamed for that attack and subsequent, larger attacks.
- Chinese security firm XLab reported the Kimwolf botnet had about 1.83 million infected devices as of December 17, 2025.
- Funnull, a content-delivery network profiled by KrebsOnSecurity, was sanctioned by the U.S. government and identified as a key source of investment/romance 'pig butchering' scams.
- Pakistani authorities arrested 21 people in May 2025 alleged to be working for Heartsender, a phishing and malware distribution service first profiled by the site in 2015.
- KrebsOnSecurity reported that 62,000 people subscribe to its plain-text email newsletter.
What to watch next
- KrebsOnSecurity plans a 2026 multi-part series investigating the origins, scale, and spread mechanisms of the Kimwolf botnet and will include a global security notification for affected devices and proxy services — confirmed in the source.
- Whether sanctions and fines (for entities like Stark and Cryptomus) will halt rebranding and asset transfers is not confirmed in the source.
- The long-term shift of large botnets from DDoS toward residential proxy rental and anonymization services, and how defenders or regulators will respond, is not confirmed in the source.
Quick glossary
- Bulletproof hosting: A type of web hosting that ignores or evades abuse complaints and takedown requests, often used to support malicious or illicit online activities.
- Botnet: A network of compromised devices controlled by an attacker and used to perform coordinated actions such as DDoS attacks, spam distribution, or proxying traffic.
- DDoS (Distributed Denial-of-Service): An attack that overwhelms a target with traffic from many sources to disrupt service availability.
- Smishing: Phishing attacks that use SMS/text messages to trick victims into revealing credentials or installing malware.
- Residential proxy: A service that routes traffic through real consumer IP addresses, often used to mask the origin of activity; such services can be abused when built on infected devices.
Reader FAQ
When was this anniversary message published?
December 29, 2025.
How many email subscribers does KrebsOnSecurity have?
The newsletter is said to have about 62,000 subscribers.
Was the site hit by a record DDoS?
Yes — in June 2025 the site experienced what was described as the largest DDoS attack Google had ever mitigated at the time, attributed to the Aisuru botnet.
Will KrebsOnSecurity investigate Kimwolf further?
Yes — the site announced a forthcoming 2026 series on the origins and spread of the Kimwolf botnet and an associated global security notification.
Who owns KrebsOnSecurity?
not confirmed in the source
December 29, 2025 0 Comments KrebsOnSecurity.com celebrates its 16th anniversary today! A huge “thank you” to all of our readers — newcomers, long-timers and drive-by critics alike. Your engagement this…
Sources
- Happy 16th Birthday, KrebsOnSecurity.com!
- Krebs on Security – In-depth security news and investigation
Related posts
- Extortion group Lovely leaks Wired subscriber data, claims 40M records
- CUII list: Domains reportedly blocked by German internet providers
- FBI Response to Fraud Allegations in Minnesota: Coverage and Context