TL;DR
A core operator known as 'Rey' has been identified as an administrator of the Scattered LAPSUS$ Hunters ransomware and extortion collective after operational-security errors linked him to a real identity in Amman, Jordan. The group has run social‑engineering campaigns targeting Salesforce and launched a new ransomware offering called ShinySp1d3r.
What happened
Scattered LAPSUS$ Hunters (SLSH), an apparent mashup of Scattered Spider, LAPSUS$ and ShinyHunters, has been extorting dozens of companies by stealing and threatening to publish internal data. Security reporting shows SLSH used voice‑phishing in May 2025 to trick targets into connecting a malicious app to Salesforce, and later published a data‑leak portal claiming Salesforce breaches at about three dozen firms, including Toyota, FedEx, Disney/Hulu and UPS. The group has solicited insiders via Telegram and has historically deployed other gangs' encryptors, but recently announced its own ransomware‑as‑a‑service, ShinySp1d3r. Investigative reporting traced the individual behind that release — an administrator known as Rey — through a series of mistakes that exposed a Telegram handle, reused credentials, infostealer data and autofill records tying the alias to Saif Al‑Din Khader, a teenage resident of Amman, Jordan who told the reporter he is attempting to leave the group.
Why it matters
- The public identification of a core operator demonstrates how poor operational security can unravel criminal anonymity and aid investigations.
- SLSH’s recruitment of insiders and voice‑phishing campaigns highlight evolving social‑engineering tactics that target cloud services like Salesforce.
- The move to offer a bespoke ransomware product (ShinySp1d3r) could increase the group’s operational reach and lower the barrier to future attacks.
- Data leak portals and mass extortion campaigns pose reputational and operational risks for a wide range of corporate victims named in the group’s claims.
Key facts
- SLSH is believed to combine members from Scattered Spider, LAPSUS$ and ShinyHunters.
- In May 2025 SLSH used voice phishing (vishing) to get targets to connect a malicious app to Salesforce.
- The group’s data‑leak portal threatened to publish internal Salesforce data from roughly three dozen companies, reportedly including Toyota, FedEx, Disney/Hulu and UPS.
- SLSH has advertised payments to insiders — employees willing to provide internal access — on its Telegram channel.
- Members previously used encryptors from ALPHV/BlackCat, Qilin, RansomHub and DragonForce; SLSH recently announced its own RaaS called ShinySp1d3r.
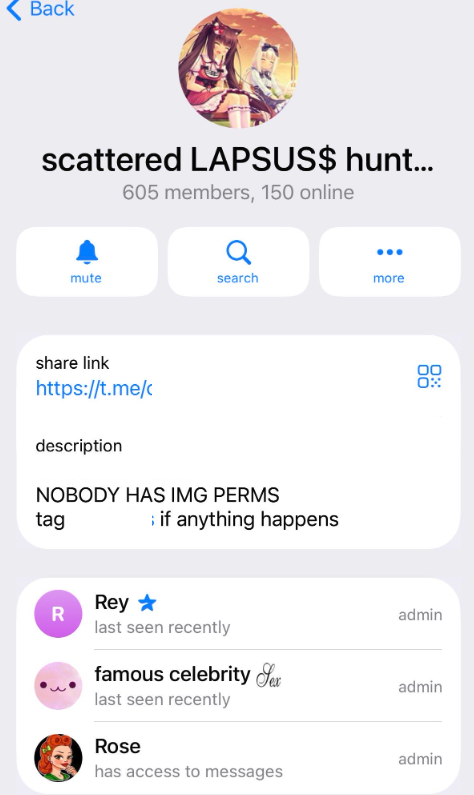
- Rey is one of three administrators of the SLSH Telegram channel and is identified as the operator who released ShinySp1d3r.
- Open‑source and commercial intelligence linked Rey’s handles across BreachForums and Telegram to an email address (cybero5tdev@proton.me) and to infostealer‑exposed credentials.
- Leaked autofill and device data indicated a shared Windows PC in Amman, Jordan, with multiple users sharing the Khader surname; an autofill entry named Zaid Khader and referenced the maiden name Ginty.
- KrebsOnSecurity contacted Zaid Khader by email; his son, identified as Saif Al‑Din Khader, messaged the reporter and said he will turn 16 next month and is trying to leave SLSH.
What to watch next
- Whether ShinySp1d3r is adopted widely by affiliates and leads to new extortion or encryption campaigns.
- Ongoing recruitment of insiders via Telegram channels and any confirmed insider‑facilitated intrusions.
- Not confirmed in the source: potential law enforcement arrests or formal charges related to Rey or other SLSH members.
Quick glossary
- Ransomware‑as‑a‑Service (RaaS): A model where developers sell or lease ransomware tools to affiliates who carry out attacks and share profits with the developers.
- Voice phishing (vishing): A social‑engineering technique using voice calls or synthesized speech to manipulate targets into revealing credentials or taking actions that compromise security.
- Infostealer: Malware that collects sensitive information from an infected device, such as saved passwords, cookies, and autofill data.
- Data‑leak portal: A public website used by extortion groups to publish or threaten to publish stolen data as leverage for ransom demands.
Reader FAQ
Who is Rey?
Rey is a core member and one of three administrators of the Scattered LAPSUS$ Hunters Telegram channel; intelligence links several online aliases to an individual identified as Saif Al‑Din Khader in Amman, Jordan.
Has Rey been arrested?
Not confirmed in the source.
Did SLSH actually steal data from major companies?
The group has claimed to have stolen Salesforce data from about three dozen companies, naming firms such as Toyota, FedEx, Disney/Hulu and UPS; the reporting describes those claims and the group’s data‑leak portal.
Is ShinySp1d3r new, and who built it?
SLSH announced ShinySp1d3r as its own ransomware service; the individual known as Rey told the reporter that it is a reworked version of Hellcat ransomware modified with AI tools.
November 26, 2025 63 Comments A prolific cybercriminal group that calls itself “Scattered LAPSUS$ Hunters” has dominated headlines this year by regularly stealing data from and publicly mass extorting dozens…
Sources
- Meet Rey, the Admin of ‘Scattered Lapsus$ Hunters’
- Scattered LAPSUS$ Hunters: portrait of an alliance
- 15-year-old revealed as key player in Scattered LAPSUS$ …
- BrianKrebs: "Scoopy, new, by me: Meet Rey,…"
Related posts
- SMS Phishers Shift Tactics: Points, Tax Refunds and Fake Shops
- How a $25M Essay-Mill Network Connects to Russia’s Synergy University
- Microsoft Patch Tuesday December 2025: 56 Fixes Including One Zero‑Day