TL;DR
A 39c3 presentation by Severin von Wnuck-Lipinski and Hajo Noerenberg examines the inner workings of modern household appliances, focusing on proprietary bus systems, hidden diagnostics and firmware. The talk demonstrates reverse‑engineering methods, discusses security protections and shows how research can enable cloud‑less integration of appliances into home automation.
What happened
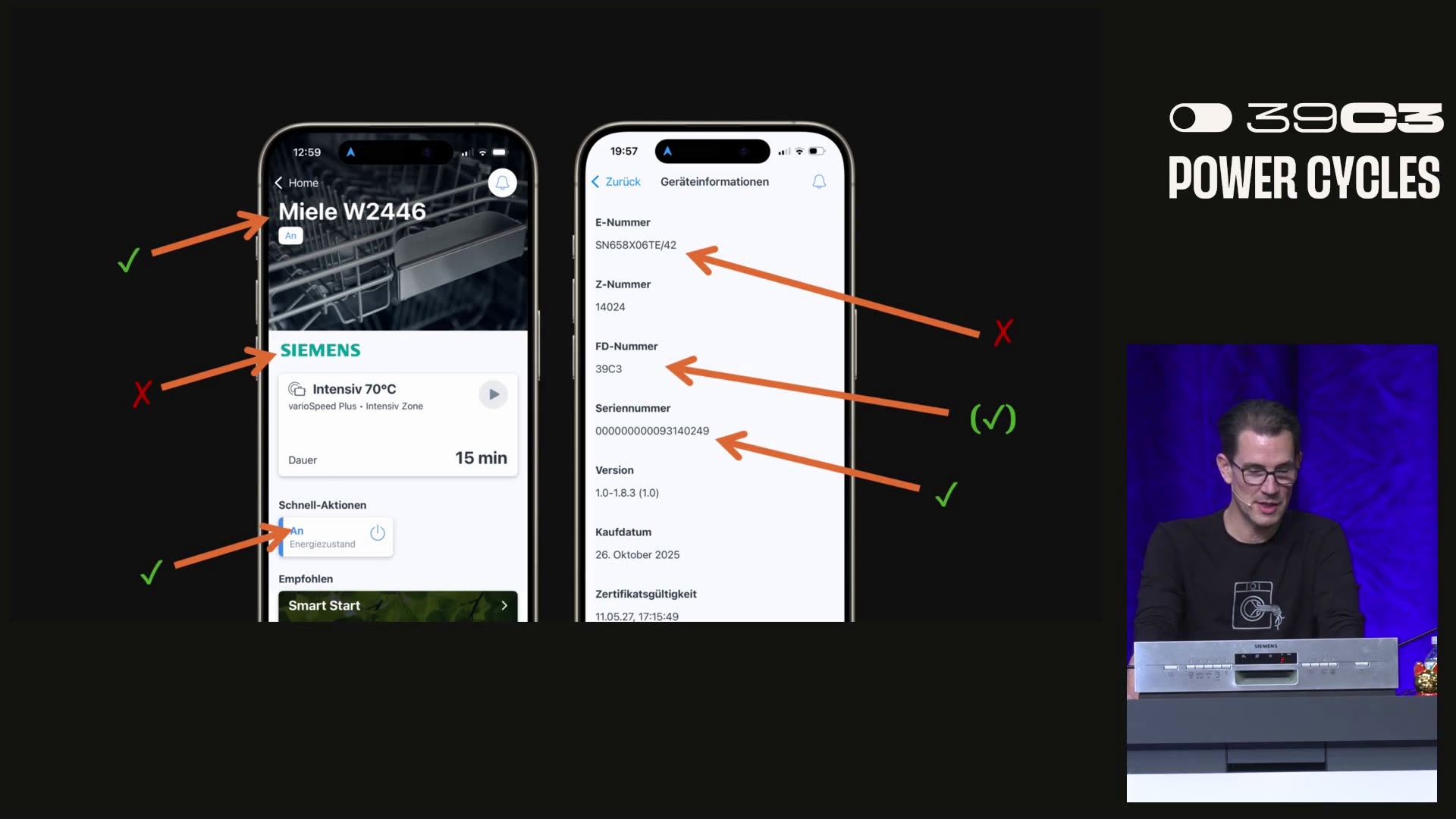
At the 39c3 conference, researchers Severin von Wnuck-Lipinski and Hajo Noerenberg delivered a roughly 57‑minute session that digs into the electronics and software inside common household appliances. The talk walks through inspection of control boards and internal communication buses, approaches to decompiling and modifying firmware, and how diagnostic interfaces are implemented and protected. The presenters describe security mechanisms meant to guard diagnostic access and firmware readout, and explain techniques they used to bypass those protections to gain deeper visibility into device behavior. As part of the presentation they show how the outcomes of this research can be applied to integrate both recent and legacy appliances into modern home automation systems without relying on vendor cloud services. The session includes examples and findings from reverse‑engineering work on appliances from B/S/H/ and Miele. The video and source files are available for download under a CC‑BY 4.0 license.
Why it matters
- Household appliances embed complex electronics and proprietary protocols that affect repairability, interoperability and security.
- Understanding diagnostic interfaces and firmware can enable local, cloud‑less integration of appliances into home automation platforms.
- Methods that bypass device protections raise questions about security controls manufacturers rely on to protect firmware and diagnostics.
- Reverse‑engineering research can inform consumers, integrators and regulators about long‑term device support and data exposure risks.
Key facts
- Presentation titled 'Hacking Washing Machines' at the 39c3 conference.
- Speakers: Severin von Wnuck-Lipinski and Hajo Noerenberg.
- Video runtime approximately 56 minutes and 57 seconds.
- Talk covers analysis of appliance control boards, proprietary communication buses and hidden diagnostic interfaces.
- Researchers discussed decompiling and modifying firmware to better understand device functionality.
- The session addresses security mechanisms for diagnostic access and firmware readout and techniques to bypass them.
- Examples and insights draw from reverse‑engineering work on B/S/H/ and Miele appliances.
- Video and supplemental files are available for download in multiple formats and languages and are licensed under CC‑BY 4.0.
What to watch next
- Whether the researchers publish tooling, scripts or firmware patches to reproduce their work: not confirmed in the source.
- Any subsequent communications from the manufacturers (B/S/H/ and Miele) about findings or mitigation steps: not confirmed in the source.
- Follow‑up research or disclosure timelines that clarify the scope of security issues uncovered: not confirmed in the source.
Quick glossary
- Firmware: Low‑level software programmed into a device's nonvolatile memory that controls hardware behavior.
- Diagnostic interface: A communication endpoint used by manufacturers or technicians to read device status, logs or to perform maintenance tasks.
- Proprietary bus: A vendor‑specific internal communication protocol used by components inside a device to exchange data.
- Decompiling: The process of translating compiled binary code back into a more human‑readable form to study program behavior.
- Cloud‑less integration: Connecting and controlling devices locally, without routing data or control through a vendor‑controlled cloud service.
Reader FAQ
Who presented the talk?
Severin von Wnuck-Lipinski and Hajo Noerenberg.
Is the video available to watch or download?
Yes — the presentation video (about 57 minutes) and associated files are available for download and are licensed under CC‑BY 4.0.
Which appliance makers were examined?
Examples in the talk draw from reverse‑engineering work on B/S/H/ and Miele appliances.
Did the talk disclose specific vulnerabilities or mitigation steps?
Not confirmed in the source.
Hacking washing machines Severin von Wnuck-Lipinski and Hajo Noerenberg Video Player 15 30 00:00 | 56:57 None eng (auto) 1.00x eng 1080p h264-hd (mp4) por 1080p h264-hd (mp4) deu 1080p…
Sources
- Hacking Washing Machines
- One – 39C3: Power Cycles Streaming – Chaos Computer Club
- BSH Bosch Siemens home appliances reverse engineering
- Hackaday | Fresh Hacks Every Day
Related posts
- Hacking Washing Machines: Reverse-Engineering BSH and Miele Appliances
- Blurring Boundaries: Rethinking Outside, Dungeon and Town in RPG Design
- Geology of the Gulf of the Farallones National Marine Sanctuary