TL;DR
Security researchers say China-based phishing groups have expanded SMS scams to include offers of rewards points, tax refunds and turnkey fake e-commerce sites that harvest card data and one-time codes to enroll cards into Apple and Google mobile wallets. Thousands of mobile-only phishing domains were registered recently; experts warn these storefronts are harder to detect than bulk smishing links and urge reporting to blocklists such as SURBL.
What happened
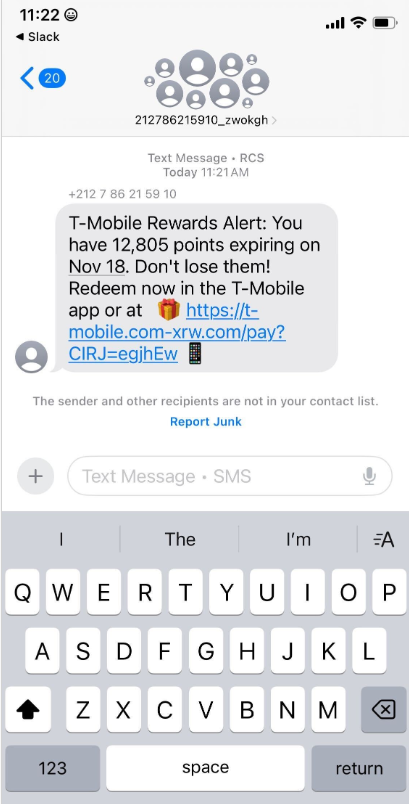
Researchers tracking recent smishing activity report that China-based phishing-as-a-service operators have broadened their lures ahead of the holidays. In the past week thousands of domains appeared that impersonate carriers such as T-Mobile and AT&T, offering large rewards point redemptions via messages sent over iMessage and RCS. The mobile-only phishing pages request personal and payment information and then prompt victims for a one-time SMS code. That code is actually triggered because attackers attempt to enroll the stolen card into an Apple or Google mobile wallet on a device they control. Investigators also found similar domains spoofing state tax agencies, with the same goal of capturing card details and one-time codes. Analysts note that these groups additionally sell phishing kits that can spin up convincing fake e-commerce shops, often advertised through search and social ads, which can remain active and unflagged for far longer than traditional smishing links.
Why it matters
- Attackers can take over victims’ payment cards by enrolling them in mobile wallets after capturing a one-time SMS code.
- Fake e-commerce storefronts are harder to detect and can remain online for extended periods, increasing victim exposure.
- Holiday shopping behavior — urgency and deal-seeking — raises the likelihood of falling for these lures.
- Mass registration of mobile-only phishing domains means a rapid, large-scale campaign that can reach many consumers.
Key facts
- Security researchers attribute the campaigns to multiple China-based phishing groups that sell phishing-as-a-service.
- Thousands of phishing domains were registered in the week leading up to the report, according to urlscan.io.
- Scam messages are being delivered via Apple’s iMessage and Google’s RCS messaging.
- Phishing pages only load for visitors using mobile devices and request name, address, phone number and payment card data.
- After card details are entered, the site asks for a one-time SMS code; attackers use that code to enroll the card in an Apple or Google mobile wallet.
- Targets identified so far include T-Mobile and AT&T customers, and spoofed state tax authorities promising refunds.
- Phishing kits include modules for rapidly deploying fake e-commerce storefronts, which are often advertised on Google and Facebook.
- Many bulk smishing domains are flagged quickly by browser vendors, but fraudulent shopping sites can evade detection and remain active for months.
- SURBL operates a reporting site, smishreport.com, which accepts screenshots of smishing messages to help blocklist new domains.
What to watch next
- A continued holiday-season surge in smishing campaigns and newly registered mobile-only phishing domains (already observed).
- Proliferation of fake e-commerce ads on search engines and social platforms that route shoppers to mobile-only fraud sites (already observed).
- Platform, carrier or law-enforcement takedown actions or disclosures related to these specific phishing kits and domains — not confirmed in the source.
Quick glossary
- Smishing: Phishing conducted over SMS or mobile messaging apps that attempts to trick recipients into revealing personal data or clicking malicious links.
- Phishing kit: A prepackaged set of tools and templates sellers provide to enable rapid deployment of phishing pages or campaigns.
- One-time code (OTP): A short-lived authentication code sent by a bank or service to verify a transaction or enrollment; attackers can use it to complete fraudulent enrollments.
- Mobile wallet enrollment: The process of adding a payment card to a digital wallet (such as Apple Pay or Google Wallet), which may require card data and an OTP.
- Blocklist (SURBL): A list of domains and IPs known to be associated with spam, phishing or malware; SURBL is a widely used blocklist service mentioned in the report.
Reader FAQ
How do these SMS scams trick victims?
Messages lure users to mobile-only sites that collect card data and then request an SMS one-time code, which attackers use to enroll the card in a mobile wallet.
What should I do if I receive a suspicious smishing message?
Do not click links; take a screenshot and report it to services such as smishreport.com, and check your card statements for unauthorized charges.
Are browsers and safe-browsing tools blocking these sites?
Many smishing domains are flagged quickly, but the report says fake e-commerce storefronts can evade detection and stay online for months.
Have carriers or platforms publicly responded to these specific campaigns?
Not confirmed in the source.
December 4, 2025 38 Comments China-based phishing groups blamed for non-stop scam SMS messages about a supposed wayward package or unpaid toll fee are promoting a new offering, just in…
Sources
- SMS Phishers Pivot to Points, Taxes, Fake Retailers
- SMS phishing tactics are becoming more sophisticated as …
- SMS phishers pivot to points, taxes, fake retailers
- Cybercriminals Pivot to Points, Taxes, and Fake Retailers in …
Related posts
- How a $25M Essay-Mill Network Connects to Russia’s Synergy University
- Microsoft Patch Tuesday December 2025: 56 Fixes Including One Zero‑Day
- Most Parked and Typosquatting Domains Now Redirect Visitors to Malware