TL;DR
Agentic coding tools like Claude Code run in sandboxes that often inherit environment variables and file access from the host, creating secret-exposure risks. The source recommends network-level controls and HTTP proxies (for example mitmproxy) plus connector-based least-privilege patterns to prevent direct leakage of credentials like Anthropic API keys.
What happened
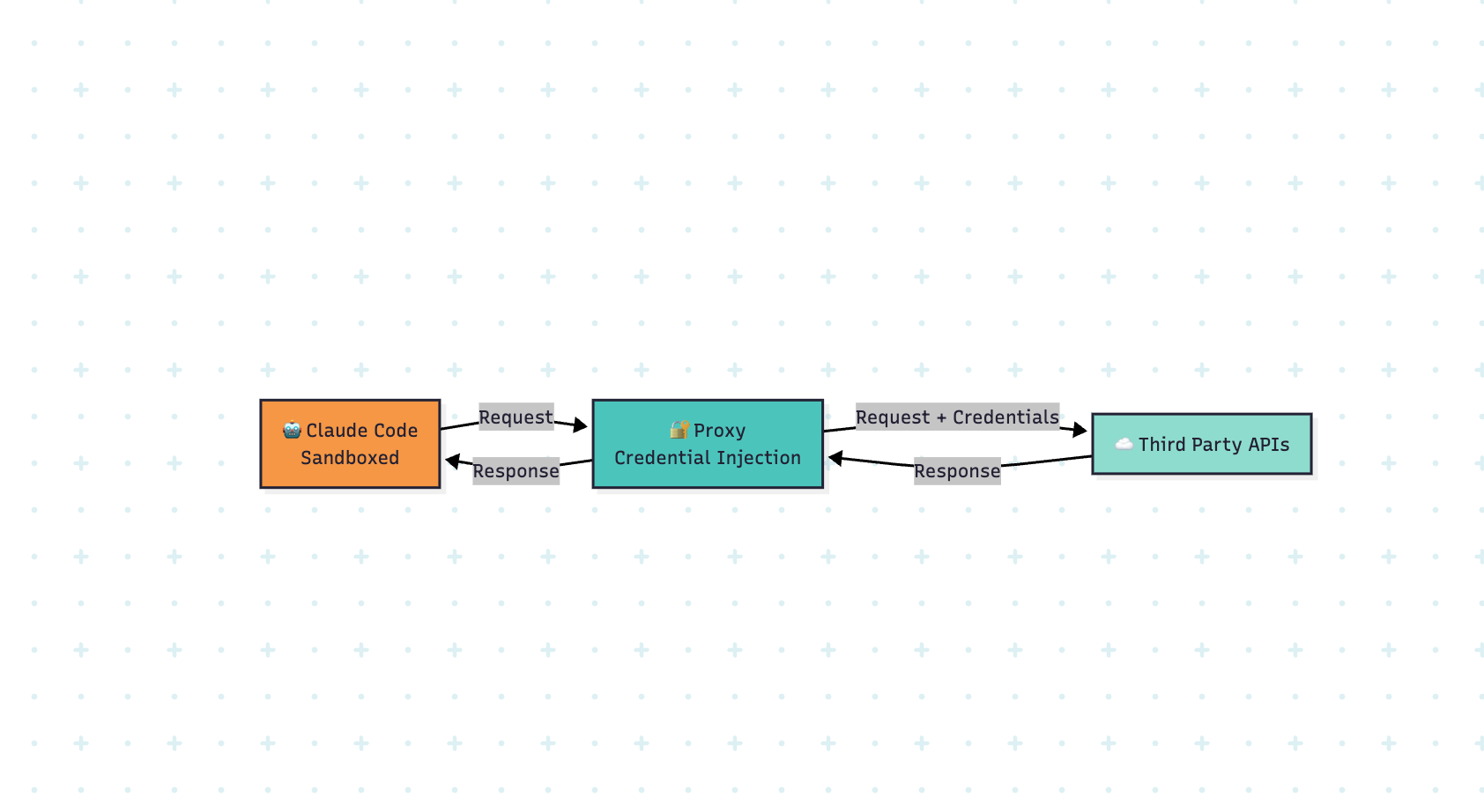
Researchers and practitioners examined how agentic coding tools such as Claude Code interact with host systems and the network, and how that interaction can leak secrets. Many macOS sandbox implementations used by Claude Code and other tools rely on sandbox-exec; Anthropic provides devcontainer templates that apply an IP-based firewall via a script (init-firewall.sh). That firewall resolves allowed hostnames to IPs and permits connections to those IPs as well as SSH on port 22. However, IP-layer allowlisting can be too coarse — application-layer routing, domain fronting, and shared infrastructure may still enable unintended actions. To address this, Claude Code supports proxy configuration through an HTTP_PROXY environment variable and a separate sandbox httpProxyPort for commands inside the sandbox. Running an intercepting proxy such as mitmproxy lets operators present dummy keys to the sandboxed process while injecting real credentials only after traffic leaves the sandbox. The post also highlights using connector services (Formal) to decouple machine and human permissions so sandboxes never hold high-privilege secrets directly.
Why it matters
- Sandboxes can still access environment variables and files from the terminal session, making local secrets vulnerable.
- IP-level allowlists are often insufficient because single IPs or CDNs can serve many hosts and actions, enabling exfiltration via allowed destinations.
- Proxies that transform requests let operators hide real credentials from the sandboxed process while still enabling legitimate API calls.
- Applying least-privilege at the application layer (connectors/resources) reduces the damage if a sandboxed agent is compromised.
Key facts
- Claude Code and other Mac tooling (Cursor IDE, OpenAI Codex CLI) use sandbox-exec for sandboxing on macOS.
- Claude Code inherits all environment variables present in the terminal session and can read files from the working directory.
- Anthropic’s devcontainer init-firewall.sh allows outbound connections to a specific host list (registry.npmjs.org, api.anthropic.com, sentry.io, statsig endpoints, VSCode marketplaces, and GitHub), resolved to IPs via dig and enforced with iptables.
- The devcontainer firewall permits inbound and outbound SSH (port 22) to any IP address.
- IP-layer enforcement can be bypassed or co-opted via infrastructure that routes by SNI/Host headers (for example AWS ALBs), and domain fronting or broad domains can be abused for diverse actions.
- Common exfiltration techniques include connecting to arbitrary SSH endpoints, publishing secrets in an npm package tarball, or creating a public GitHub gist.
- Claude Code supports proxies in two places: an HTTP_PROXY environment variable for the parent process and a sandbox httpProxyPort for bash commands inside the sandbox; the two are independent.
- Mitmproxy can intercept TLS traffic if its CA certificate is provided to node processes (NODE_EXTRA_CA_CERTS) and can run addons to rewrite requests and inject real API keys after interception.
- Admin Anthropic API keys inherit the full permissions of the user who created them; API keys issued from the Claude API appear to have restricted endpoint access but exact permissions are undocumented.
What to watch next
- Whether Anthropic publishes clearer, fine-grained controls and documentation for API key permissions: not confirmed in the source.
- Broader adoption of proxy-based interception workflows or formal connector integrations to keep high-value secrets out of sandboxes: not confirmed in the source.
Quick glossary
- Sandbox: An isolated runtime environment that restricts what code can access or do on the host system.
- Proxy: A server that forwards network requests and responses, often used to inspect, filter, or modify traffic between a client and a target service.
- mitmproxy: An interactive HTTPS proxy tool that can intercept, inspect, and modify HTTP(S) traffic; often used for debugging and traffic transformation.
- Domain fronting: A technique where requests appear to go to an allowed domain or IP but are routed to different services based on routing or headers, complicating allowlist-based controls.
Reader FAQ
Can Claude Code access my environment variables and local files?
Yes. Claude Code inherits environment variables from the terminal session and can read files in the directory where it runs.
Will an IP-based devcontainer firewall fully prevent secrets exfiltration?
No. IP-layer allowlisting can be too coarse because single IPs or infrastructure can host multiple domains or route based on headers; SSH access on port 22 and other channels remain possible.
Can I hide my Anthropic API key from Claude Code?
You can present a dummy key to the sandbox and use a proxy (for example mitmproxy with an addon) to inject the real key after interception; note a required OAuth sign-in step may complicate this flow.
Are Anthropic API keys fine-grained?
Admin API keys inherit the creating user’s full permissions. Claude API–generated keys appear to have endpoint restrictions, but exact permissions are not documented in the source.
Sandboxing agentic coding tools is a networking problem Allowlisting commands on a trusted host for an agentic coding tool can be somewhat fraught. Taking inspiration from Simon Willison: Sandboxes help…
Sources
- Using proxies to hide secrets from Claude Code
- making Claude Code more secure and autonomous
- Sandboxing – Claude Code Docs
- How Claude Code's Sandboxing Solves the Approval …
Related posts
- YC-backed Sei Seeks Senior DevOps Engineer in Gurugram and Chennai
- Windows info-disclosure zero-day patched after CISA adds it to catalog
- Why Yarn Spinner Is Avoiding Generative AI in Its Tools