TL;DR
A recent phishing campaign is using compromised SendGrid customer accounts to send politically charged bait that bypasses normal email authentication. Recipients are urged not to click links; SendGrid users should enable two-factor authentication and check for unauthorized API keys.
What happened
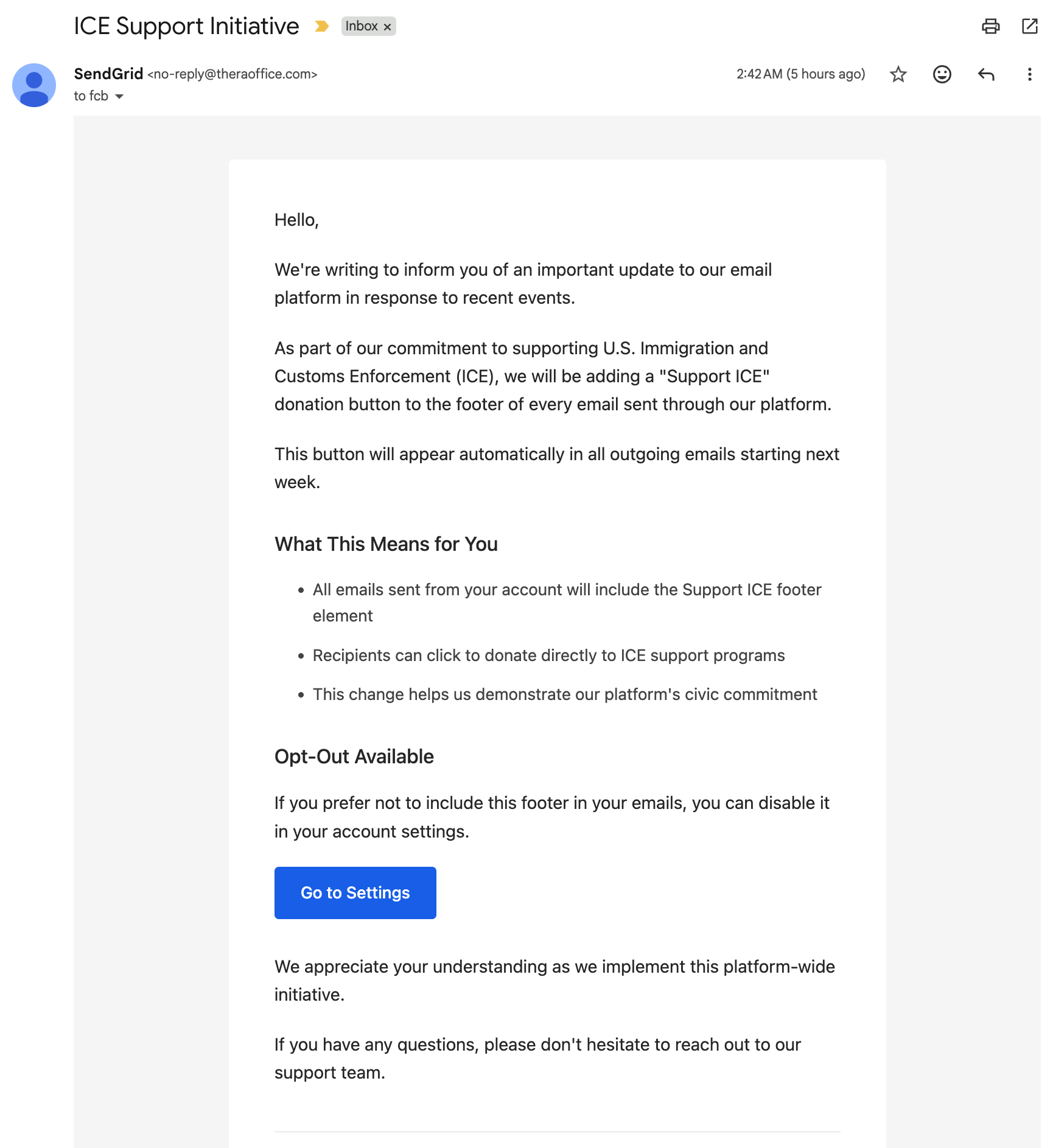
The author has been receiving a steady stream of deceptive emails that appear to come from legitimate SendGrid customers. Attackers gain access to SendGrid customer accounts (via common methods such as credential reuse and stuffing), then send phishing messages through SendGrid’s infrastructure. Because these emails originate from real SendGrid users, they pass SPF and DKIM authentication checks and often land in inboxes as if they were legitimate. Recent lures have been tailored to provoke strong emotional responses by referencing US political flashpoints — examples include fake announcements about LGBT-themed footers, Black Lives Matter commemoration themes, an alleged “Support ICE” donation button, a sudden Spanish-language switch, and classic account-termination notices. Security researchers described this technique as “Phishception” in 2024; observers note the tactic has been reported as far back as 2020. Links in these messages lead to realistic fake login pages that can capture credentials and even one-time codes in real time.
Why it matters
- Emails sent from compromised SendGrid customer accounts can bypass standard spam filters because they pass SPF and DKIM checks.
- Politically charged messages are designed to provoke quick clicks, increasing the risk of credential theft.
- Compromised accounts can be reused to target more SendGrid users, creating a self-amplifying threat.
- Failure to adopt basic protections like unique passwords and two-factor authentication keeps the attack surface large.
Key facts
- SendGrid is an email delivery service owned by Twilio.
- Attackers compromise SendGrid customer accounts and send phishing emails through those accounts’ infrastructure.
- Because the messages are sent via genuine SendGrid customers, they pass SPF and DKIM authentication checks.
- Security researchers (Netcraft) labeled this tactic “Phishception” in 2024; Brian Krebs wrote about similar activity in 2020.
- Examples of recently observed lures include fake announcements about pride footers, Black Lives Matter themes, a supposed “Support ICE” button, a Spanish-language switch, and account termination notices.
- Sender domains in these phishing examples are often legitimate businesses whose SendGrid accounts appear to have been taken over.
- Phishing links point to realistic fake SendGrid login pages that can validate credentials against the real SendGrid API and capture two-factor codes.
- Recommended protections for SendGrid customers include enabling two-factor authentication, using unique passwords, and checking for unauthorized API keys or sender identities.
- A simple Gmail filter can help: block messages that mention SendGrid but are not from sendgrid.com or twilio.com (steps provided in the source).
What to watch next
- Whether Twilio/SendGrid will move from discussion to mandatory enforcement of two-factor authentication — not confirmed in the source.
- The emergence of additional politically tailored lures or new social-engineering themes aimed at specific communities.
- Any public disclosure from Twilio/SendGrid about mitigation steps, or data on the scale of compromised customer accounts — not confirmed in the source.
Quick glossary
- SendGrid: A cloud-based email delivery service used by businesses to send transactional and marketing messages; owned by Twilio.
- SPF / DKIM: Email authentication standards (Sender Policy Framework and DomainKeys Identified Mail) that help verify a message was sent by an authorized mail server.
- Phishing: A social-engineering attack where attackers send deceptive messages to trick recipients into revealing credentials or clicking malicious links.
- Two-factor authentication (2FA): An additional login security layer that requires a second form of verification (such as a code) beyond a password.
- Credential stuffing: An attack method where attackers try lists of stolen username/password pairs across many services, exploiting reused credentials.
Reader FAQ
Am I being targeted if I receive one of these emails?
Receiving one of these messages does not necessarily mean your account is compromised; attackers are targeting people who have used SendGrid or are likely to recognize it.
What should I do if I get a suspicious SendGrid-looking email?
Do not click links. Verify sender domains and, if you use SendGrid, log in directly to your account to check for unauthorized activity.
Is this an attack on SendGrid itself?
The source indicates attackers are taking over customer accounts and using SendGrid’s infrastructure to send phishing emails, rather than compromising SendGrid’s core systems.
Are state actors responsible for these campaigns?
Not confirmed in the source; the author notes state actors have used similar tactics historically but says this operation could also be run by non-state threat actors.
Why is SendGrid emailing me about supporting ICE? Written by Fred on January 9, 2026 For the past several months, I’ve been receiving and then ignoring a steady stream of…
Sources
- Why is SendGrid emailing me about supporting ICE?
- Phishing in the Cloud: SendGrid Campaign Exploits Account
- SendGrid/Twilio Phishing Alert
- SendGrid is abused to host phishing attacks impersonating …
Related posts
- Report: Vietnam government alleged to bar rooted phones from banking apps
- Senators Urge Apple to Remove X and Grok from App Store Over AI Abuse
- iOS 26 Lets You Replace Apple Defaults — New Categories and Regions